What is DMARC?
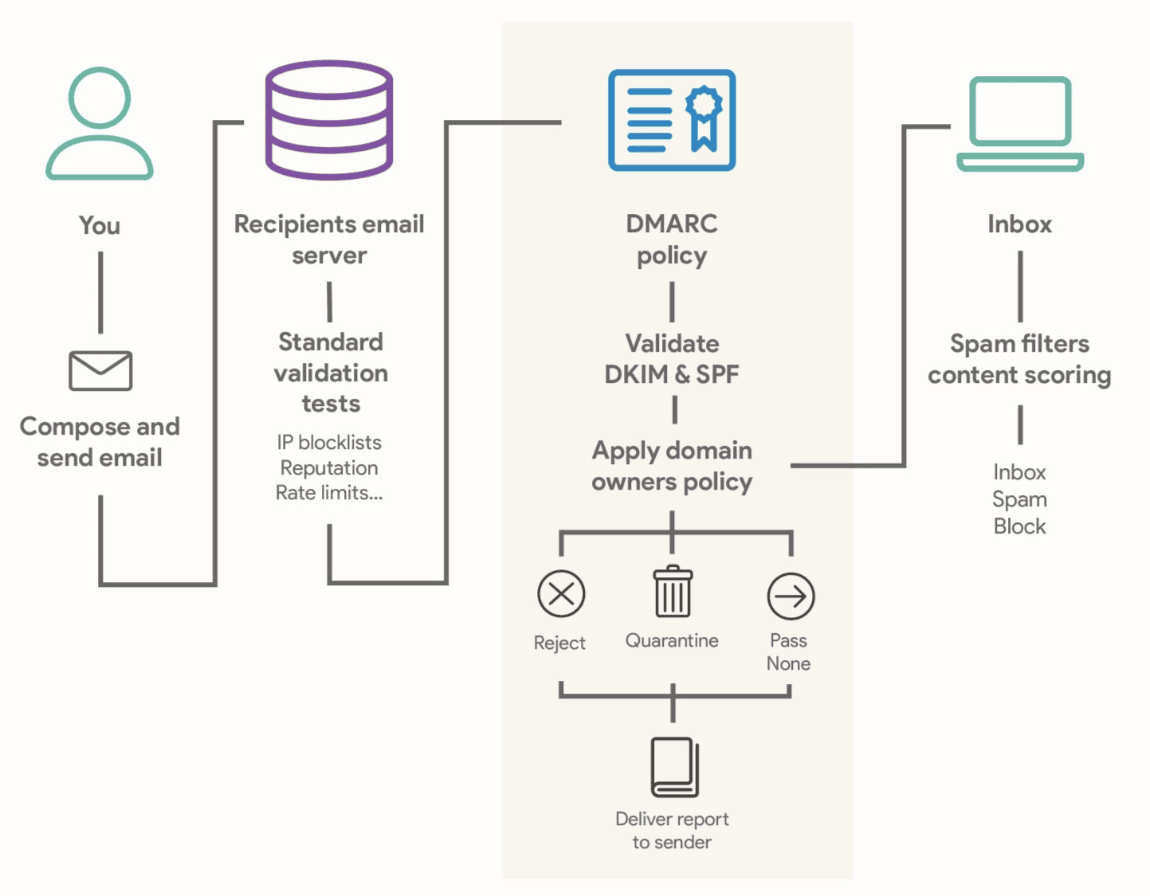
How DMARC Works
- SPF and DKIM Check: The recipient's mail server checks if the email passes SPF and DKIM authentication.
- DMARC Policy Evaluation: Based on the configured DMARC policy (none, quarantine, or reject), the server determines what to do with the email.
- Reports Sent: The recipient’s mail server sends DMARC reports back to the domain owner, providing insights into email activity and unauthorised email attempts.
Why Has DMARC Adoption Been Slow?
- Complexity of Implementation - Setting up DMARC requires proper configuration of SPF and DKIM records, which can be confusing for businesses without dedicated IT teams.
- Risk of Email Deliverability Issues - If DMARC is misconfigured, legitimate emails could be rejected or marked as spam, disrupting communication. This risk makes many hesitant to enforce strict policies.
- Lack of Awareness - Many businesses don’t realise that their domains can be exploited for email spoofing. Without awareness of the risks, there’s little urgency to adopt DMARC.
- Perceived as a ‘Big Business’ Solution - Some SMEs believe DMARC is only necessary for large enterprises, not realising that any domain can be targeted by email fraud.
- The "Set It and Forget It" Mindset - Some companies implement DMARC at the none policy level for reporting purposes but never move to stricter enforcement (quarantine or reject).
How to Set Up DMARC for Your Domain
Step 1: Set Up SPF (Sender Policy Framework)
2. Locate the DNS settings for your domain.
3. Add a TXT record with the following format:
- Replace mailprovider.com with your email service provider (e.g., Google Workspace, Microsoft 365).
- The "-all" means that emails not listed in SPF should be rejected.
4. Save the record and allow time for propagation.
Step 2: Set Up DKIM (DomainKeys Identified Mail)
Step 3: Configure DMARC
- p=none: This starts DMARC in monitoring mode (change to quarantine or reject later).
- rua: Email address to receive aggregate reports.
- ruf: Email address to receive forensic reports.
- pct=100: Applies the policy to 100% of emails.

